Penetration testing, also known as pen testing or ethical hacking, is a simulated cyber attack against a computer system, network, or web application to test its security.
Penetration testing, also known as pen testing or ethical hacking, is the process of testing a computer system, network, or web application to find vulnerabilities that an attacker could exploit. A penetration test can be used to assess the security of a system and identify any weak points that need to be addressed.
The main goal of penetration testing is to identify vulnerabilities that could be exploited by attackers.
Penetration testing Sydney, also known as pen testing or ethical hacking, is the process of testing a computer system, network, or web application to find vulnerabilities that could be exploited by attackers.
The main goal of penetration testing is to identify vulnerabilities that could be exploited by attackers. By doing so, organizations can take steps to mitigate these risks and reduce the likelihood of an attack.
Penetration tests can be conducted manually or with automated tools. Manual testing typically requires more time and resources but can be more thorough and effective in identifying potential security issues. Automated tools are typically faster and require less manpower, but may not be as effective in identifying all potential vulnerabilities.
Organizations should consider their needs and objectives when deciding which type of penetration test to conduct. In general, penetration tests should be conducted periodically to ensure that systems are secure and up-to-date with the latest security patches.
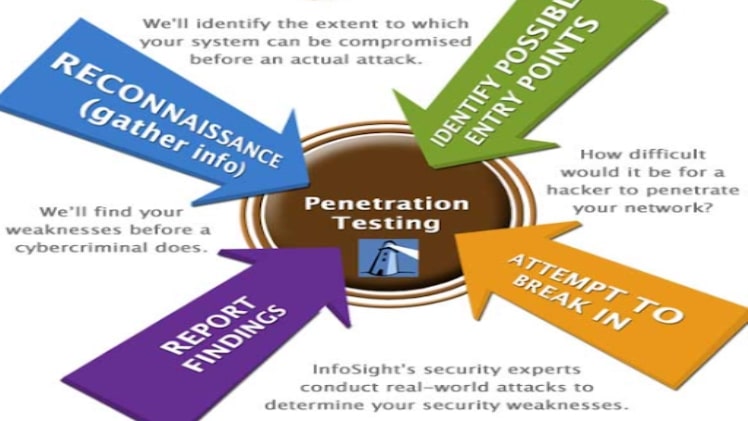
Penetration tests can be conducted manually or with automated tools.
Penetration tests are used to assess the security of a computer system or network. They can be conducted manually or with automated tools.
Manual penetration testing is conducted by ethical hackers who attempt to bypass security controls and gain access to sensitive data. This type of testing can be time-consuming and expensive, but it is often considered the most effective way to identify vulnerabilities.
Automated penetration testing tools are used to scan for weaknesses in systems and networks. These tools can be less effective than manual testing, but they are much faster and less costly. Automated testing is often used as the first step in penetration testing, followed by manual testing if necessary.
Once vulnerabilities are identified, they can be fixed to improve the security of the system.
There are many benefits to improving the security of a system by fixing vulnerabilities that have been identified. For one, it can help to prevent attackers from exploiting those vulnerabilities to gain access to the system. Additionally, it can also help to deter would-be attackers from even attempting to attack the system in the first place. Finally, fixing vulnerabilities can also improve the overall stability and reliability of the system.

